GNSS Spoofing Land Vehicles
Description
GNSS signal spoofing consists of broadcasting fake signals –over the real GNSS signals– in order to take control of a GNSS receiver that will continue to track those signals in error. GNSS is very sensitive to this type of attack due to the weakness of satellite signals at the earth’s surface and the fact that these signals are public and not protected as such. A successful spoofing attack consists of taking control of a receiver without it noticing the attack. The goal of the attack is to introduce an erroneous result for position or timing or both.
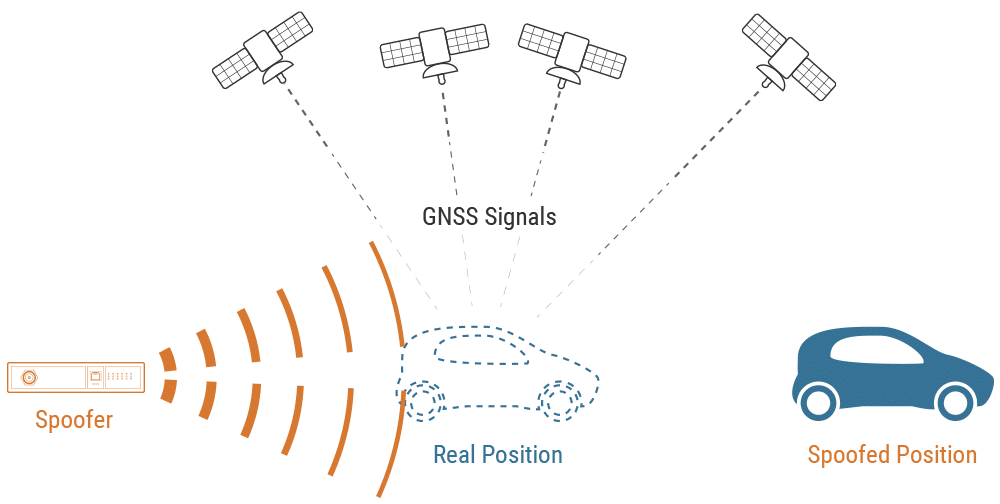
Spoofing differs from jamming in that a successful attack is not noticed by the receiver. A successfully jammed receiver will typically lose its calculated position/speed/time (PVT) result, which is easily detected by the equipment itself or the master system.
With critical systems, solutions exist for addressing a missing GNSS result. Jamming is therefore relatively well accounted for in practice, without critical impact. However, a successful spoofing attack can induce errors in the receiver without any protective mechanism taking notice. It is easy to imagine the potentially disastrous consequences of spoofing on an airliner, a banking system, or an electrical grid.
As a first step, a spoofing resistant receiver should therefore detect the attack and ideally, in the second step, be able to recover the genuine GNSS calculation result. Unfortunately, the protection of GNSS receivers was treated as an afterthought for a long time, because of the increased complexity involving spoofing attacks when compared to jamming. Since the turn of the century, an effective, evolved spoofing attack has required the procurement of GNSS constellation simulators costing hundreds of thousands of dollars or developing complex equipment yourself. Today, the growing popularity of cheap and powerful software defined radio (SDR) equipment makes this a clear and present danger.
Every manufacturer or integrator of GNSS receivers should therefore include robust spoofing resistance testing as part of its certification process. These tests should be performed with the aid of a GNSS simulator because it is not feasible to broadcast false GNSS signals in the open sky. Thanks to its ability to synchronize multiple radios and sessions, Orolia’s Skydel GNSS simulator is designed to address these types of scenarios.
This application note describes the procedure for performing a spoofing attack, in a controlled environment, on a vehicle in order to test the receiver’s robustness in such a scenario. Other tests could have been performed; for example, testing the robustness of a time-based spoofing attack.
It is important to note that this document is limited to explaining how to assess a receiver’s ability to resist and overcome spoofing via simulated GNSS signal but does not provide a method for spoofing actual GNSS signals as such. That is a much more complex undertaking and, for security and ethical reasons, is outside the scope of this document.
Test procedure
In this example, we demonstrate how to perform a spoofing attack on a vehicle travelling from point A to point C. During the trajectory, a spoofer will attempt to take control of the vehicle’s GNSS receiver to instead take the vehicle to point D. The split in trajectories occurs at point B —towards the midpoint of the scenario— and the attack takes place before this separation. Acquiring control of a receiver consists of sending identical GNSS signals, since the trajectories are the same up until separation, but with a slight initial delay.
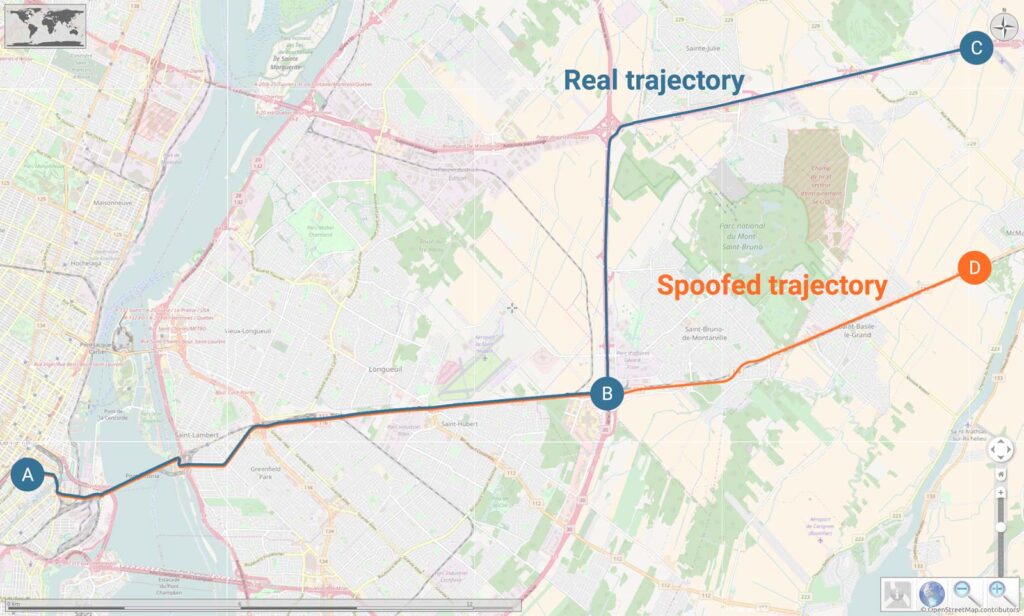
During the simulation, this delay decreases until the real and spoofed GNSS signals overlap. It is at this moment that the spoof attack succeeds, with the spoofer taking control of the receiver; it remains locked on to the spoofer whose timing advance will continue to increase, in order to distance itself from the authentic GNSS signals.
Since tracking multiple constellations is usually considered to be an effective protection against spoofing, we evaluated this scenario in the following modes:
- The GNSS receiver in GPS mode and the spoofer transmitted in GPS mode as well
- The GNSS receiver in GPS/Galileo mode and the spoofer transmitted in GPS mode only
- The GNSS receiver in GPS/Galileo mode and the spoofer transmitted in GPS/Galileo mode as well
- The receiver is considered to be perfectly resistant to an attack if it does not deviate from its trajectory and it continues to point C
When under attack, the GNSS receiver will most likely compute temporary PVT errors of a few meters. We consider errors of this magnitude acceptable if the receiver continues to follow the authentic signals. Nevertheless, a receiver is considered vulnerable if its trajectory continues towards point D and no alert is reported. (Note: the GNSS receiver tested in this scenario does not feature a spoofing alert).
Configuration
| Simulator | |
|---|---|
| Skydel | Version 17.1.7 |
| Timing Reference System | Octoclock-G |
| Software-Defined Radio (SDR) | 2 x ETTUS USRP X300 |
| Controller PC | Nvidia GeForce GTX 1080 Intel Core 17-69700K Windows 10 Pro |
Test set-up
The configuration used for this spoof testing is shown in the following illustration:
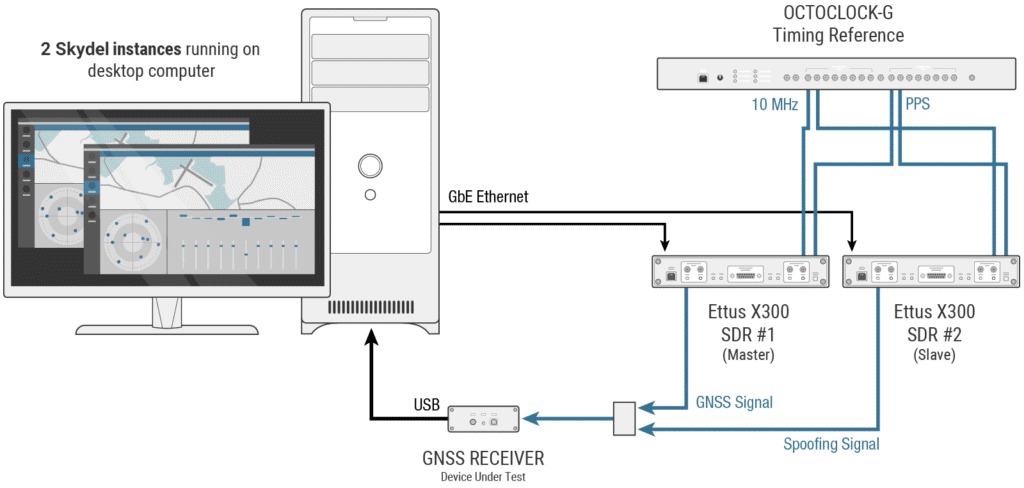
The PC hosting the Skydel simulator is connected to two USRP X300 radios. One of the radios—the master—represents the authentic GNSS signal while the other radio—the slave—represents the spoofer. Here we are using one of the most powerful features of the Skydel simulator, which is the ability to synchronize as many radios as we want among themselves (with one master and as many slave radios as we desire). It is sufficient to distribute common 1 PPS and 10 MHz signals to each of the radios; in this case, the signals are provided by an Octoclock precision clock. Each radio is controlled by a different Skydel session, operating on a single PC. In the case where the PC and its graphic card are not powerful enough to run 2 multi-constellation simulations in parallel, it would be possible to synchronize between 2 remote PCs.
The GNSS signals from the two radios are then combined and sent to the GNSS receiver. The receiver is connected to a PC via USB in order to view its position in the Skydel simulator.
Test Details
Due to the sensitive nature of the subject of spoofing, the complete test details and its procedures, including scripts, can be provided on demand to existing Skydel clients and only after a screening process. Please Contact Us for additional details.
Results
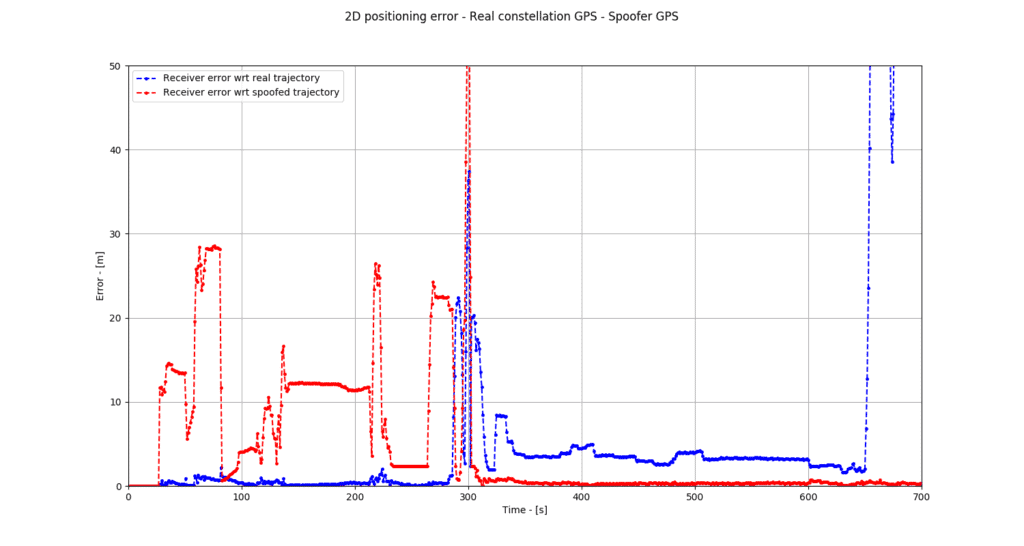
The figure 1 below represents the positional error (2D space) between the receiver’s position and the true simulated position (in blue), the positional error (2D space) between the receiver’s position and the spoofed position (in red). Analysis of the results demonstrates the following success in spoofing GPS with a GPS spoofer:
- Between t = 0 s and t = 300 s, the error between the signals is minimal, which indicates that the receiver is tracking the real signal correctly.
- Around t = 300 s, is the moment when the spoofer is able to take control of the receiver. We can see here that the takeover was successful since the error with the spoofer decreases where the error with the real signals increases. It is important to note that, at the time of transition, the real signals error hits 50 m before stabilizing. The takeover is not completely transparent from the point of view of the receiver and could be detected with specific algorithms.
- From t = 660 s onward, the two trajectories diverge and there is no longer any doubt that the spoofer has achieved its objective of taking control.
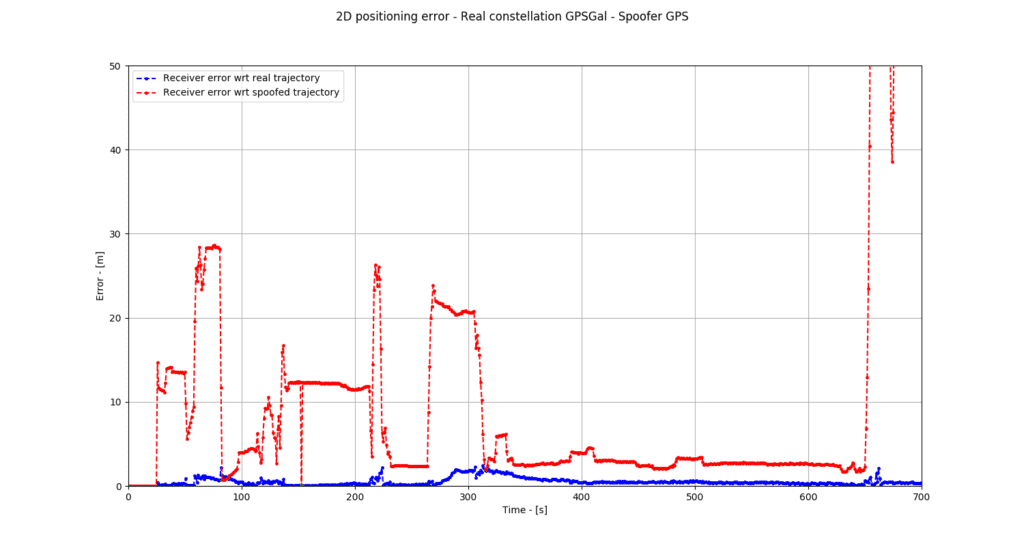
In the second test, the receiver follows the GPS and Galileo signals while the spoofer only operates in GPS mode. We can see here (figure 2) that the error remains minimal relative to the actual position whereas it is much higher relative to the spoofed one. The attack failed, which we can confirm from 660s, when the two positions diverge.
A detailed analysis shows that the validity of the GPS position varies significantly while the Galileo position remains true and stable. In conclusion, the dual-constellation approach offers relatively effective protection against a simple spoofing.
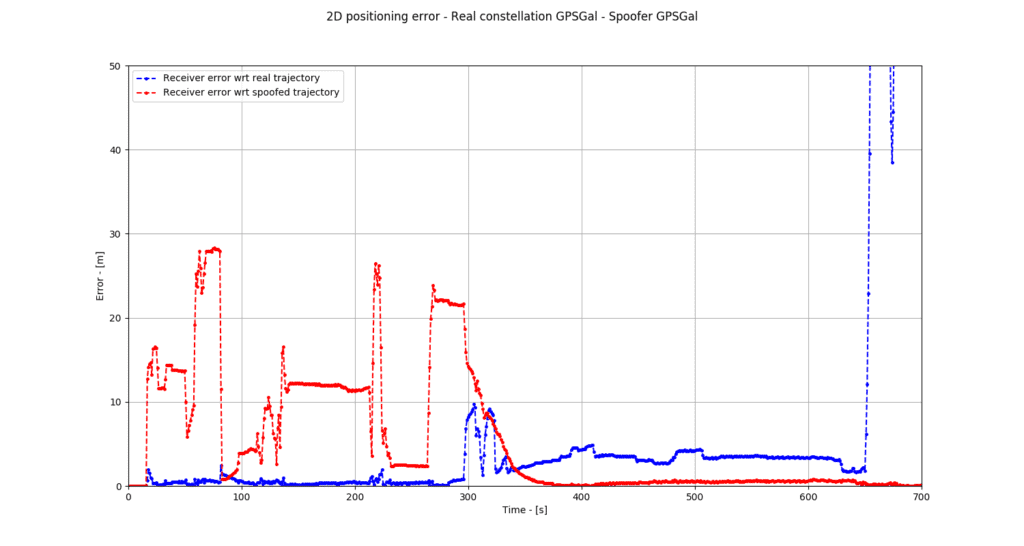
Finally, during the final test (figure 3), the receiver followed the authentic and spoofed GPS / Galileo signals equally. The results are similar to those from the first test, where a dual-constellation configuration did not protect the receiver.
Conclusion
In conclusion, this application note has described how to configure the Skydel simulator to validate the ability of a receiver to respond to a spoofing attack. While various other spoofing tests could be performed, the configuration would stay largely the same. This use case provides a glimpse of the possibilities provided by the Skydel simulator regarding the synchronization of multiple sessions and radios.
Furthermore, the test results demonstrate the ease with which one can spoof a receiver, including when it is configured in multi-constellation mode. This speaks to the importance of taking this type of threat into account when designing a receiver and validating its robustness in the face of a spoofing attack.


