Why Would Unmanned Systems Need PNT Solutions?
Unmanned system ecosystems rely on accurate PNT Data
The term “Unmanned Systems” includes all autonomous aircrafts, vehicles or vessels as well as remotely piloted ones – through wireless communication with a command and control center- that carry a payload specific to a mission priority such as surveillance, sensor data collection, or surveying.
Their reliance on Global Navigation Satellite System, or GNSS, signals can put a global unmanned vehicle’s ecosystem at risk in case of interferences or cyberattacks that might affect reception of satellite transmission and, therefore, provide the ecosystem with corrupted timing, navigation or positioning data.
Because unmanned systems rely partially on GNSS signals to get the most accurate positioning data, the entire ecosystem might be at risk in case of interferences on GNSS signals or even worse, GNSS-denied environment.
Type of threats that might affect GNSS signals
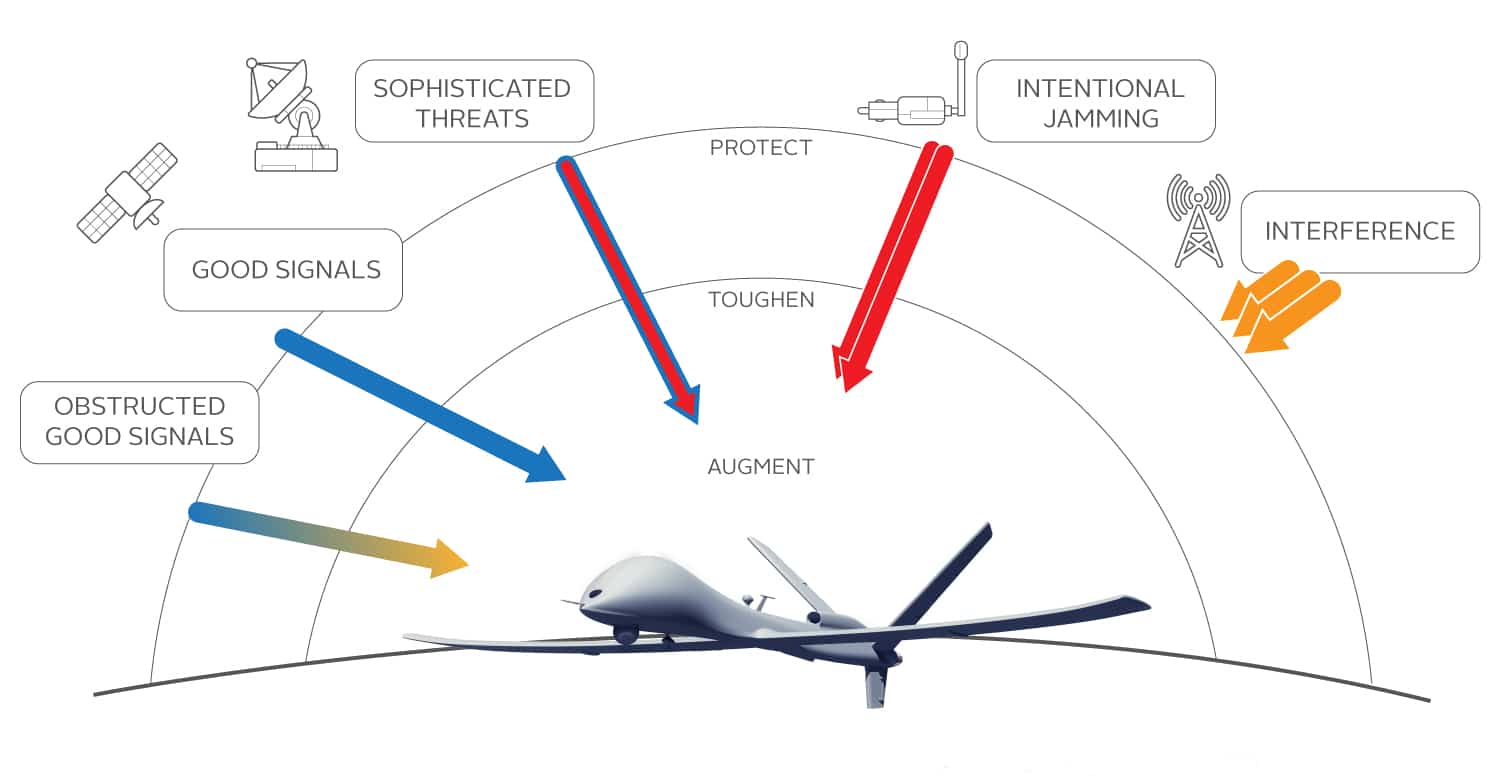
Various threats, ranging from intentional to environmental, can directly impact GNSS signal reception:
- Jamming: Intentional interference targeting the unavailability of the system.
- Spoofing: Sophisticated attack that provides inaccurate information about both location and time by generating fake GNSS signals.
- Cyberattacks: Attacks launched from one or more computers against another computer, multiple computers or networks.
- Signal Obstruction: Loss of signal due to obstruction in the line of sight to a satellite.
- Signal Degradation: Unintentional signal interference due to environmental factors or other RF signal interference.
The need for dedicated solutions to protect the integrity and accuracy of PNT data is rising with increasing demand for unmanned systems in both military and private sector applications. The COVID crisis has increased the need for improved situational awareness, intelligence, and safety for military and civilians.
The impact on critical GNSS-reliant infrastructures
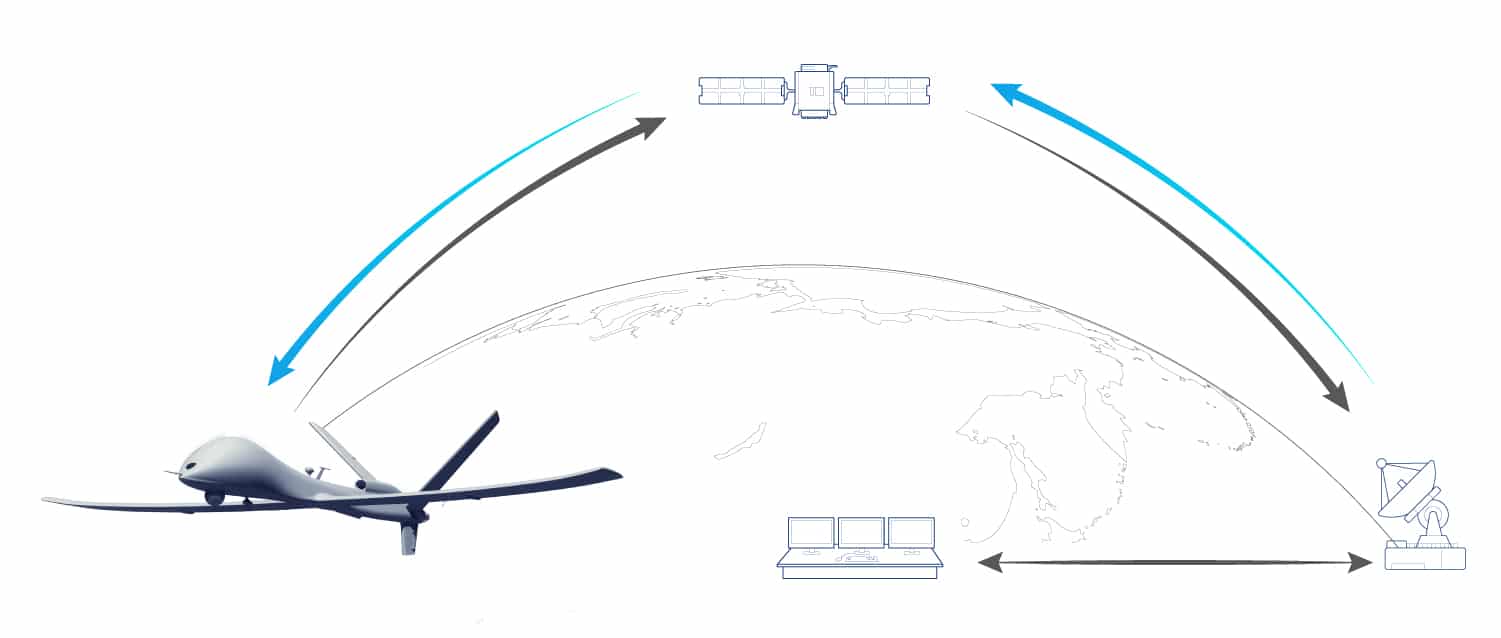
Unmanned System infrastructures are mostly dependent on GNSS signals. Applications relying on accurate PNT data can have multiple vulnerabilities in the ecosystem, from the control center to the unmanned vehicle itself.
Here is a short overview of the type of applications or infrastructure that might be at risk of receiving compromised PNT data:
- Control Center: Control Centers require accurate PNT data to enable operators to remotely control the aircraft, vehicle or vessel. GNSS applications should incorporate monitoring technology, such as Internial Measrement Units (IMU), to provide continuous PNT output during times of intermittent GNSS outages and to provide an internal check against spoofing.
- Data Link: Data links allow real-time transmission of data collected by the Unmanned System. If signals are compromised or lost, navigation can be jeopardized as well as the integrity of synchronization and network data.
- Payload: Common payloads include Intelligence, Surveillance and Reconnaissance (ISR) equipment that requires ruggedized Geo time-stamping in order to receive precise both location and time of data collection.
The Orolia PNT Advantage
From timing and synchronization to GNSS simulation, Orolia delivers the accuracy, reliability, and ruggedization, required to ensure critical data collection, navigation, and continuous operations, even in GNSS-denied environments.
As unmanned systems rely on Positioning, Navigation and Timing (PNT) data for remote navigation control, payload sensors and other GNSS-based applications, Orolia will be able to provide dedicated solutions for several types of applications to ensure PNT data protection:
- Sensor Synchronization: GNSS signal interference can impact the timing synchronization of embedded sensors, potentially compromising data collection on the navigation computer. By using an atomic clock as holdover oscillator, sensor data will be synchronized even in GNSS-denied environments.
- Continuous Communication: Accurate time and frequency information, even in GNSS denied environments, is a key enabler of high-speed and secure datalinks between the UAV and ground control. By using a time server equipped with jamming detection software, this continuous transmission will be maintained.
- Accurate Navigation Data: In case of a spoofing attack, embedded sensors might receive compromised data to make the unmanned vehicle drift from its initial trajectory. By protecting the embedded navigation device with integrated anti-jammer, PNT data will be secured and reliable.
- Battlefield Readiness: In case of a spoofing attack, embedded sensors might receive compromised data, causing the unmanned vehicle drift from its initial trajectory. By testing unmanned vehicles before sending them on the field, you will be able to configure them properly to react to jamming and spoofing attacks.


